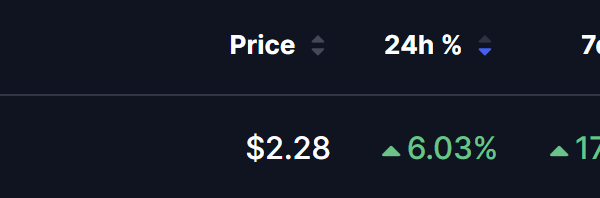
The Internet Computer has taken a significant step towards enhancing blockchain security with the approval of Proposal 140407, which establishes its inaugural TEE-enabled subnet. This move aims to foster what the project terms “hardware-rooted trust,” an essential aspect for enterprise-level blockchain implementation.
This newly activated subnet comprises a cluster of seven nodes, marking a pivotal shift from traditional software-based security measures to a model that enforces confidentiality at the hardware level. For the first time, canisters operating within this TEE environment can execute processes in a fully confidential manner, ensuring that sensitive data remains inaccessible not only to external parties but also to the executing nodes.
Trusted Execution Environments, or TEEs, are designed to address a critical vulnerability present in conventional computing setups. Typically, data must be decrypted while in a server”s memory during processing, which creates a window for exposure to malicious actors or compromised infrastructure. In contrast, TEEs, such as the AMD SEV-SNP technology deployed in this subnet, isolate computations within a secure enclave inside the processor. This ensures that data is decrypted exclusively within the processor die, preventing access by the operating system or hardware owners, and allows for remote attestation to confirm that the code within the enclave remains unchanged.
The introduction of TEEs is heralded as a transformative advancement for the Internet Computer, particularly since it already allows for the hosting of complete applications on-chain. Previously, applications dealing with highly sensitive data—like medical records, proprietary algorithms, or private communications—relied on trust in decentralized node operators. With TEE-based execution, this trust pivots from the operators to the hardware, facilitating a broader range of enterprise and privacy-focused applications.
Notable use cases include confidential on-chain AI models, where user inputs and model parameters are shielded from node operators, as well as enterprise solutions that must adhere to stringent data protection regulations such as GDPR or HIPAA. The new subnet is currently in a controlled testing phase with seven nodes, fewer than the typical thirteen, attributed to the enhanced security guarantees provided by TEEs. Access is limited while developers accumulate operational insights and prepare for a wider rollout.
Looking ahead, the project”s roadmap indicates that TEE-enabled subnets will likely become a standard offering for developers. Future implementations may permit canisters to be deployed on either public subnets or specialized TEE subnets, depending on the specific needs of applications. This upgrade is seen as a foundational leap toward broadening the Internet Computer”s capabilities and providing a privacy-preserving framework within its overarching “world computer” architecture.