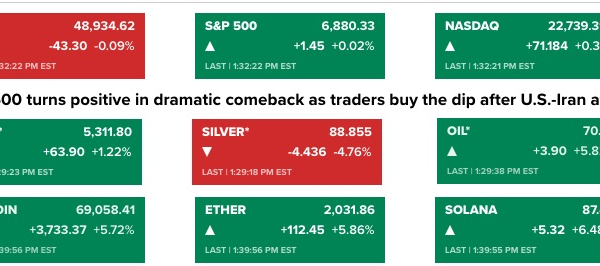
The DeadLock ransomware group, which surfaced in July 2025, has gained attention for its innovative exploitation of Polygon blockchain smart contracts. According to a report from cybersecurity firm Group-IB, the group utilizes these smart contracts to manage and frequently rotate proxy server addresses, making it increasingly challenging for cybersecurity defenders to permanently block their malicious infrastructure.
Once a victim”s system is compromised, DeadLock deploys an HTML file that serves as a conduit for messages via the decentralized messaging platform Session. Through embedded JavaScript code, this file queries a designated Polygon smart contract to retrieve the current proxy URL, enabling the transmission of encrypted communications between the victim and the attacker”s Session ID. Notably, these queries are read-only and do not incur any transaction fees, allowing the attackers to maintain operations at no cost.
Group-IB researchers highlighted the unique nature of this technique, which provides attackers with a seemingly limitless array of variations, thus complicating detection efforts. Despite being underreported, this approach is reportedly gaining traction among malicious actors. A separate investigation by Cisco Talos revealed that DeadLock typically gains initial access by exploiting CVE-2024-51324, a vulnerability linked to Baidu Antivirus, employing a method known as “bringing your own vulnerable driver” to disable endpoint detection and response systems.
What sets DeadLock apart from its peers is its departure from the conventional double extortion model commonly adopted by ransomware groups. Instead of operating a data leak site, it threatens to sell stolen data on underground markets while offering victims security reports and a commitment not to re-target them if the ransom is paid. Although Group-IB”s tracking efforts have not connected DeadLock to established ransomware affiliate programs, they identified smart contract copies created and updated between August and November 2025.
Furthermore, the group has successfully tracked its infrastructure through blockchain transactions, revealing distinct funding patterns and active servers. Interestingly, similar techniques have been noted among nation-state actors, with the Google Threat Intelligence Group observing North Korean threat actor UNC5342 using a related method named EtherHiding for malware delivery and cryptocurrency theft since February 2025. EtherHiding involves embedding malicious code, often JavaScript payloads, within public blockchain smart contracts.
As a layer-2 solution built on Ethereum”s infrastructure, Polygon presents both opportunities and risks. While DeadLock remains a low-volume threat at present, experts warn that its innovative techniques highlight a skill set that could pose significant risks if organizations fail to recognize the seriousness of the threat. In response to this evolving landscape, Group-IB advocates for businesses to enhance their security measures, including implementing multifactor authentication, conducting employee training, and maintaining up-to-date data backups. They emphasize the importance of not paying the ransom and instead contacting incident response experts promptly in the event of an attack.