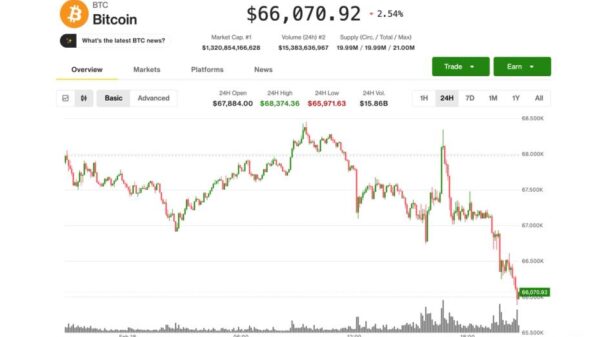
The Algorand Foundation has unveiled a detailed security framework for AI-assisted blockchain development, coinciding with the recent $1.78 million breach of the Moonwell decentralized finance (DeFi) protocol. This incident was attributed to an oracle configuration error stemming from code generated through a practice known as “vibe coding.” The foundation”s initiative aims to address the growing concern over security vulnerabilities in applications developed with casual AI prompting across the Web3 landscape.
In the announcement, Gabriel Kuettel highlights a critical distinction between “vibe coding” and “agentic engineering.” This terminology, introduced by Google”s Addy Osmani, underscores the need for developers to take an active role in the coding process. Vibe coding involves soliciting AI suggestions without thorough review, which can lead to errors and significant risks. In contrast, agentic engineering emphasizes the developer”s control over the architecture while utilizing AI for implementation, thereby enhancing speed without significantly increasing liability.
The implications of security breaches in the blockchain space are far more severe than in traditional Web2 applications. In scenarios where conventional apps suffer data leaks, users often have recourse through identity protection, dispute mechanisms, or legal actions. However, vulnerabilities in smart contracts can result in immediate and irreversible loss of funds, with no possibility for rollback or refunds.
The newly established framework by Algorand identifies several critical areas where AI may pose risks to developers:
- LocalState vs. BoxMap: AI systems may default to using LocalState for user balance storage, but this can lead to data loss if users clear their local state. The framework insists that for critical data, developers should utilize BoxMap.
- Key Isolation: Citing research from Peter Szilagyi, the framework advocates for a complete separation between AI agents and private keys to maintain security integrity.
- Agent Skills: Developers are encouraged to use curated instruction sets that incorporate best practices, thus avoiding deprecated APIs and outdated patterns commonly found in AI-generated code.
Another notable recommendation is to utilize AI tools as adversaries rather than solely as builders. The VibeKit”s simulate_transactions feature allows developers to test attack vectors without engaging the network directly. This functionality was recently showcased by a community member who successfully simulated unauthorized admin access and other vulnerabilities within a sandbox environment.
Algorand”s protocol already mitigates certain vulnerability classes, such as reentrancy attacks, but potential AVM-specific vulnerabilities remain. The framework”s simulation tools provide developers with a cost-effective way to assess security risks.
Interestingly, those developers already acquainted with Algorand”s security model will likely derive the most benefit from these AI tools. For less experienced developers, however, AI can act as a valuable educational asset, turning each generated contract into a learning opportunity. Engaging with the AI to understand its decision-making processes can help prevent oversights, as evidenced by the lessons learned from the Moonwell breach.
As AI-assisted development tools continue to evolve, the disparity between what should be launched on MainNet and what is actually deployed is widening. Algorand”s framework aims to bridge this gap and ensure developers are aware of the risks they face in this rapidly advancing technological landscape.